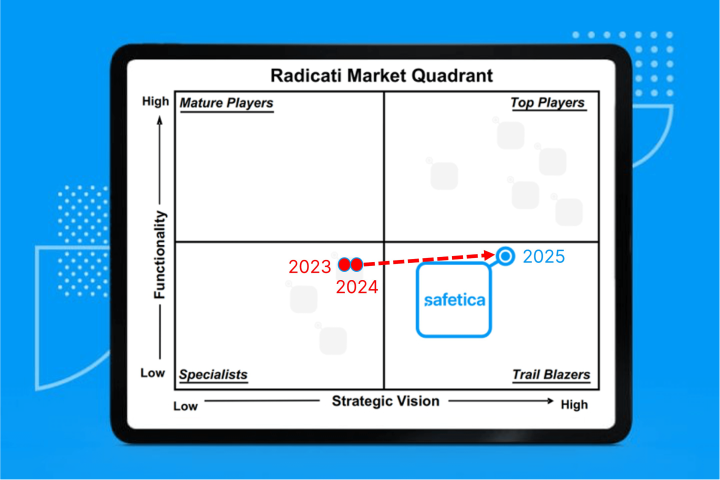
Knowledge base
Terms, definitions, information. Start here if you want to learn more about Safetica solutions.
e-Learning
Do you want to learn in a systematic manner? Just choose your course and start exploring the word of of Safetica and insider threat protection.
Webinars and events
From online webinars to meetups and technology fairs... here is a list of all Safetica events.