Trusted by organizations around the globe:






What is Insider Risk?
Insider risk encompasses potential threats from trusted insiders, including employees. These risks vary from inadvertent actions like human error to deliberate malicious activities.
This highlights the importance for organizations to not only enhance productivity but also implement measures to detect and mitigate insider threats effectively.
Non-malicious insider risk continues to pose the greatest risk to organizations
56%
of insider-related incidents caused by a negligent employee
86 days
average time it takes for organizations to detect and contain an insider threat incident
$16.2M
average cost of insider threat incidents
Accurately spot insider threats and stop them
Safetica provides proactive protection against insider threats, taking swift action to safeguard crucial data.
Our solution effectively blocks data exfiltration through diverse channels, including cloud services, email, websites, removable storage devices, and more.
Safetica combines insider risk management with employee productivity insights.
Safetica offers a comprehensive solution that not only fortifies your data against insider risks but also optimizes your team's performance.
Our solution provides real-time monitoring and analysis of user activities, identifying insider threats, blocking risky actions, and uncovering shadow IT, while also offering alerts and reports for enhanced workspace security.
ANALYZE USER ACTIVITIES
Gain detailed insights into how your team operates, from file transfers to messaging, ensuring both productivity and security.
MITIGATE INSIDER THREATS
Identify potential risks originating from within your organization, safeguarding your sensitive data.
REAL-TIME ALERTS & NOTIFICATIONS
Stay in the loop with instant notifications for blocked activities, ensuring uninterrupted workflows.
VISUALIZE USER BEHAVIOR TRENDS
Understand how your team functions and make informed decisions for further improvements.
IMPROVE RESOURCE USAGE
Get precise overview whether purchased hardware and software licenses are distributed and used efficiently
ACTIONABLE REPORTS
Access reports tailored to your needs, providing valuable insights for process enhancement.
Why Safetica
Continuous Monitoring and Auditing
Safetica offers real-time monitoring and audit trails that provide full visibility into data access and usage, supporting compliance and security efforts.
Zero-Day Threat Detection & Response
Safetica's proactive identification and immediate response to emerging threats ensure protection against zero-day vulnerabilities
Behavioral Analytics & Anomaly Detection
Safetica's advanced behavioral analytics identify suspicious activities and anomalies, enabling early detection and mitigation of potential security breaches.
Schedule a Demo
See how Safetica can disover, classify, and protect your most valuable data through a personalized demo.
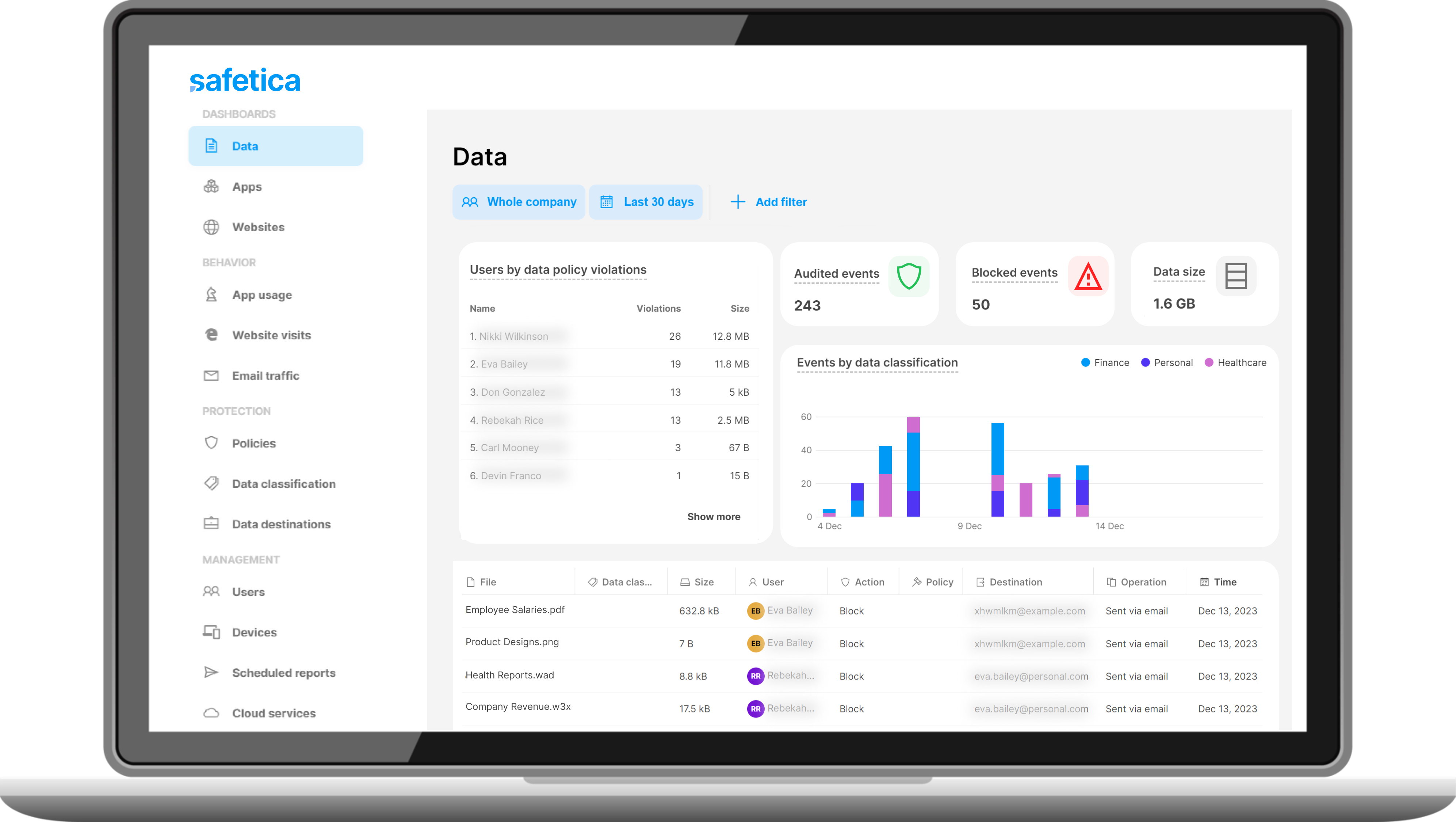
Learn more about insider risks



