Technology is at the heart of business operations. Companies invest heavily in IT infrastructure and applications to support operations, increase efficiency, and improve productivity. However, despite the growing sophistication of corporate IT, employees are increasingly turning to unauthorized technology solutions to address their specific needs, leading to a phenomenon known as Shadow IT.
What is Shadow IT?
Shadow IT is any technology or software used within an organization without the knowledge or approval of the IT department. This includes cloud-based services, applications, and devices bought and managed by employees or departments rather than the IT department.
Examples of shadow IT
- WeTransfer, Imgur and other online file transfer/image sharing services
- Gmail, Drive and other Google Suite elements
- Dropbox, Box and other peer-to-peer collaboration tools
- WhatsApp and other messaging apps
Shadow IT hardware includes:
- Personal laptops
- Smartphones
- USB flash drives
Why Do Employees Use Shadow IT?
The reasons for using Shadow IT vary, but one of the primary drivers is the need for employees to be productive and efficient in their work. Often, corporate IT systems and software are not tailored to meet the specific needs of individual departments or employees. This can lead to frustration and the search for alternative solutions to meet their needs more effectively.
In addition, the pace of technological change is such that employees may feel that IT departments need to catch up with the latest tools and services. By using Shadow IT, employees may feel that they can stay ahead of the curve and remain productive.

Risks of Shadow IT
The use of Shadow IT poses significant risks to organizations, including:
- Security Risks: Shadow IT applications are often not vetted for security, leaving organizations vulnerable to cyberattacks and data breaches.
- Compliance Risks: Many Shadow IT solutions do not comply with regulatory requirements such as GDPR, HIPAA, or PCI DSS, leading to potential compliance issues.
- Data Loss Risks: Data stored in Shadow IT solutions may not be backed up, leading to potential data loss in the event of a hardware failure or system outage.
- Operational Risks: Shadow IT solutions can cause conflicts with existing corporate IT systems, leading to operational disruptions.
How to Manage the Risk of Shadow IT
To manage the risks of Shadow IT, companies should:
- Educate Employees: Employees need to understand the risks of Shadow IT and the importance of following corporate IT policies.
- Establish Clear IT Policies: Companies should create clear policies that outline which applications and services may be used within the organization.
- Provide Alternative Solutions: Companies should work with employees to find authorized solutions that meet their needs.
- Monitor and Enforce Policies: Organizations should watch for Shadow IT and enforce policies and procedures to prevent unauthorized use.

Don't Let Shadow IT Sneak Up on You with Safetica NXT
Through the Shadow IT feature of Safetica NXT, the admin user can conveniently review the company's software and web application catalog and keep track of any unwanted applications or websites. Safetica NXT's intelligent analysis and automated risk detection make this task effortless.
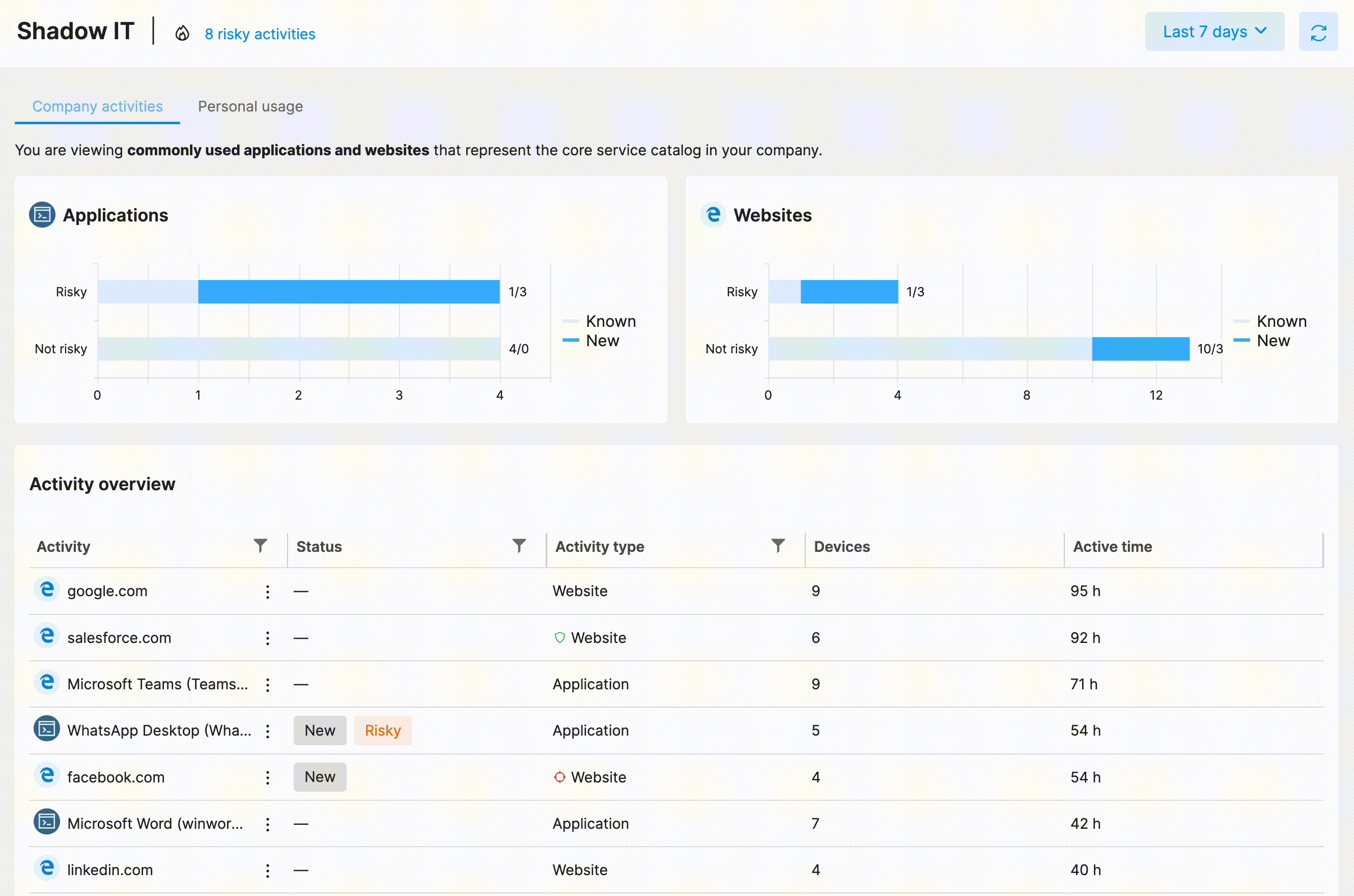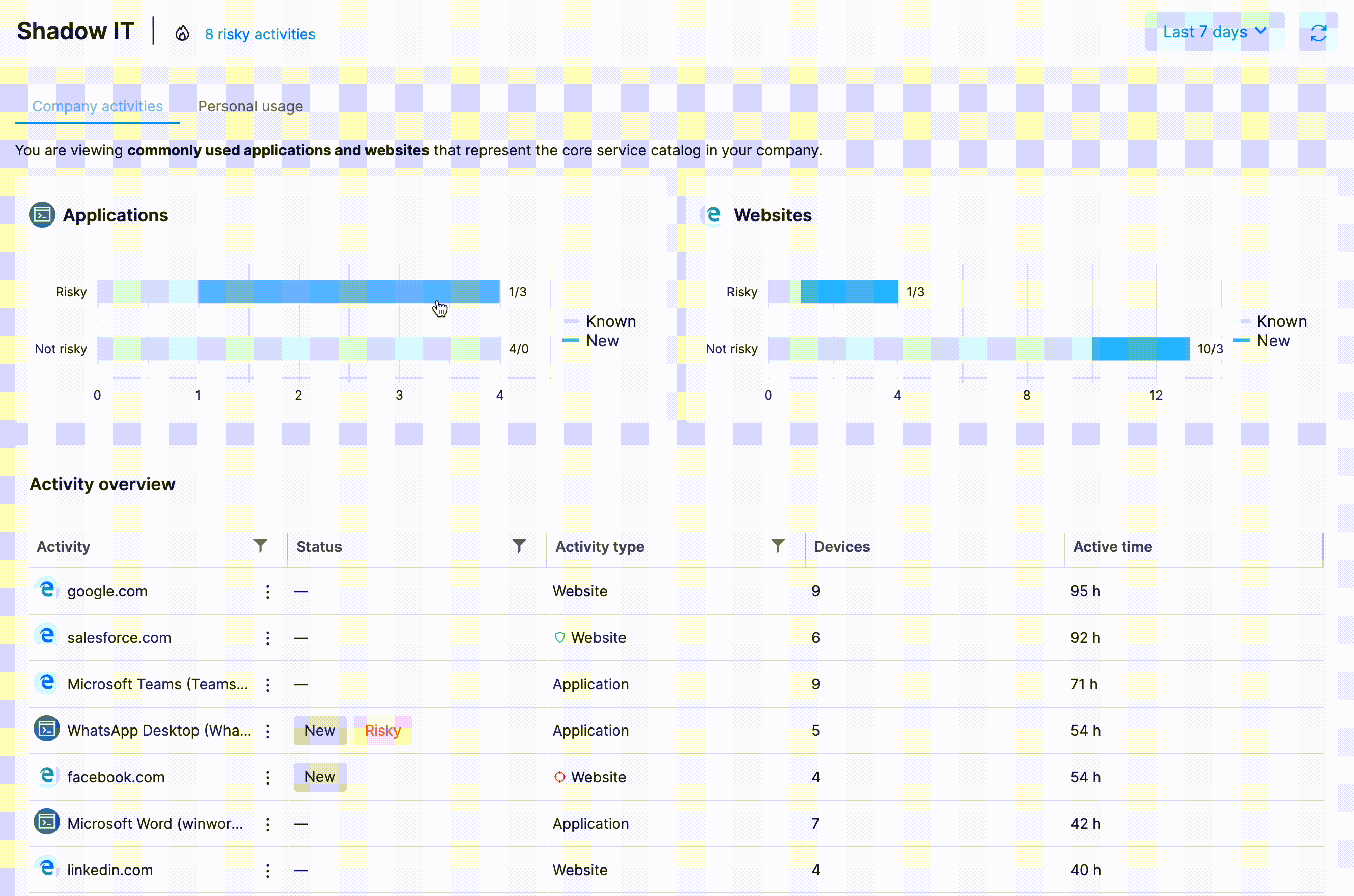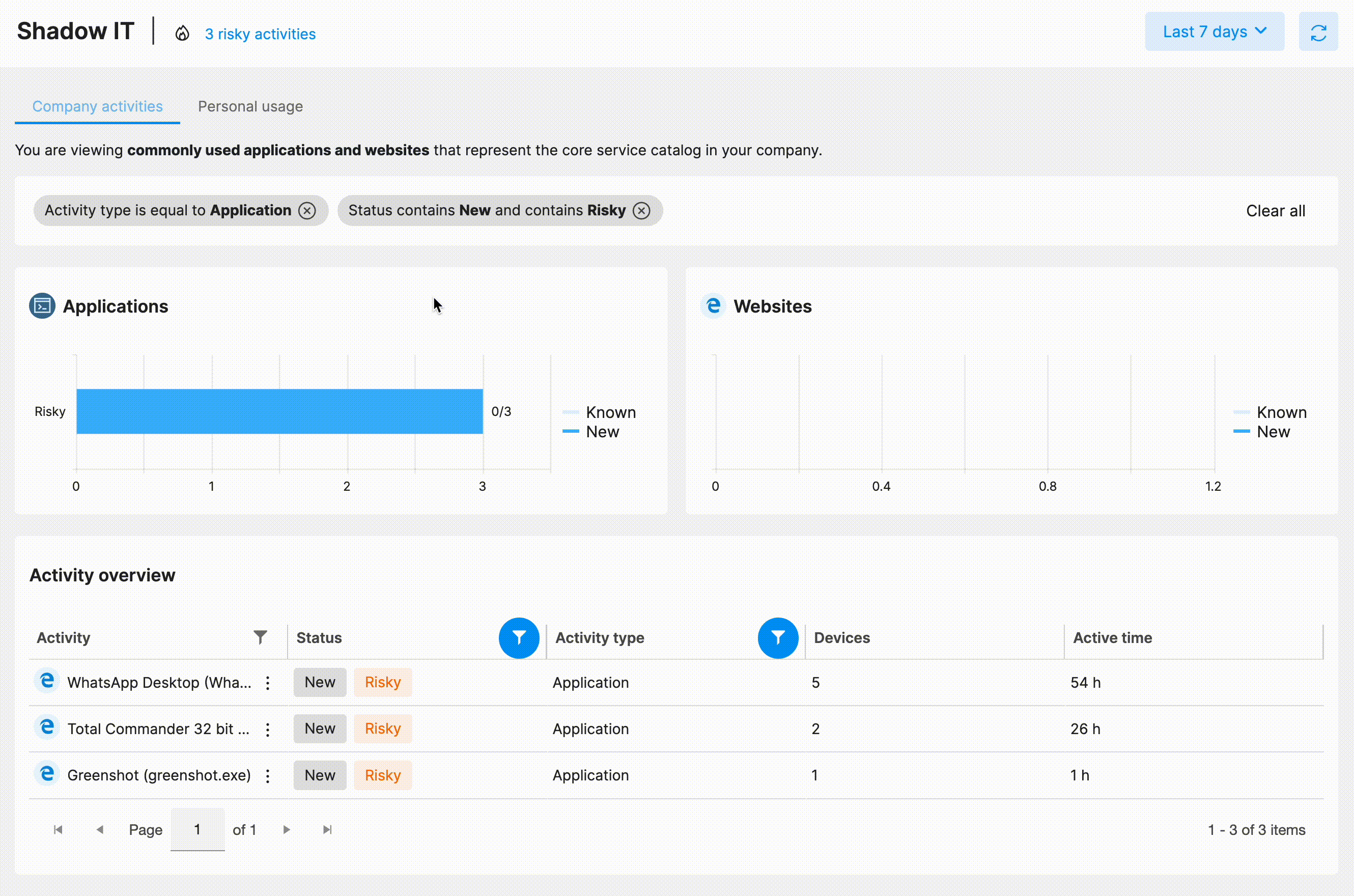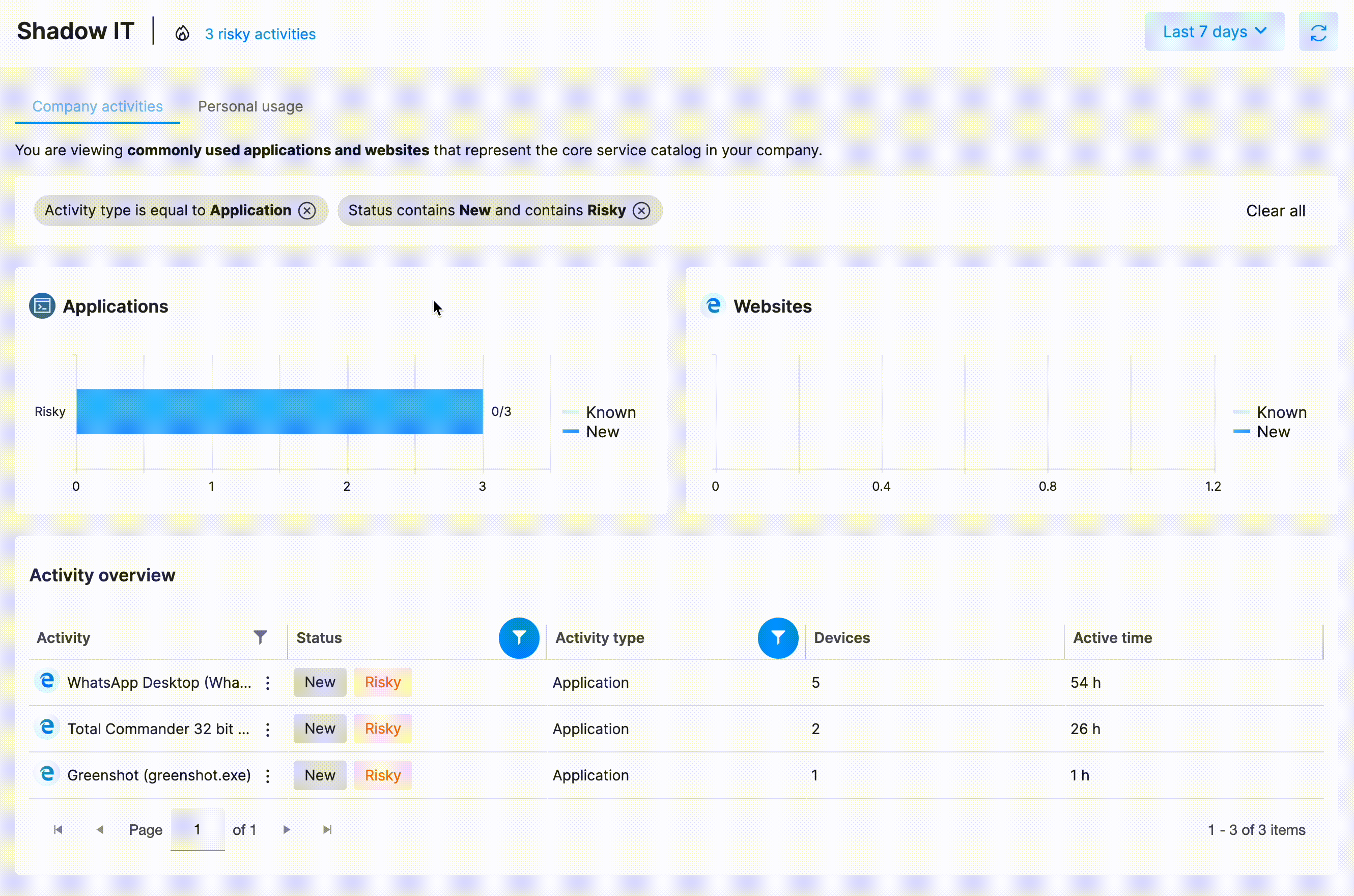
The Shadow IT section consists of two tabs:
Company activities
This default tab includes all the significant application or website activities, whether approved or Shadow IT. Any newly detected activity is flagged, especially those deemed risky. Related file operations are easily accessible to see whether a suspicious activity might lead to a data breach.
Personal usage
Safetica NXT automatically filters harmless personal activity records into the Personal Usage tab. The records in this tab are subject to privacy control, ensuring that sensitive personal data is kept secure. However, if an administrator needs to perform a deep dive while investigating a security incident, they can access these records to get a complete picture of what happened.
As you can see, Shadow IT is a significant threat to corporate security, and organizations must take steps to manage its risks. By educating employees, creating clear policies, providing alternative solutions, and monitoring and enforcing policies, companies can reduce the risks of Shadow IT and ensure the safety and compliance of their IT infrastructure.
For more information about how Safetica can help reduce the risk of Shadow IT in your organization, download the datasheet or start your free trial today.
Next articles


