Do you know where all your company’s data is and how it flows through your operations and processes? Company data flows on both official and unofficial channels, such as email, cloud, printers, instant messaging, etc. If employees don’t treat data with the proper care, it can very easily be lost. Read more about data protection – why it is important and how to do it best.
In this article you will learn:

How companies produce data
Business data is any information that is relevant for running a company. There are two types of data – input data and output data. Input data is provided by the users, and computers provide output data.
Companies gather data from various sources and channels, and they do so via different software or AI. More sophisticated tools are used for Big Data processing.
Examples of data that companies usually have:
- Financial information
- Company strategic information (long-term vision, business objectives, staff development, equality and diversity, etc.)
- Business and sales forecasts
- Customer information
- Personal data
- Website traffic statistics
- Campaign details (social media, emailing, etc.)
- Sales results
- Warehouse and inventory data
- HR data (employee information, salaries, interactions between teams, etc.)
- Customer and partner information from CRM systems
- Source code
- Blueprint and designs
What is data flow
Data flow is the movement of your company’s data throughout your systems. Data can flow via both software and hardware and can be changed during the process of moving.
Different employees and teams have access to the data at specific points in the data flow. They can change data, provide data to other departments or vendors, or even delete data.
Data can leak at any moment, and every stage of the data flow can be risky in terms of data protection.
Where companies store their data
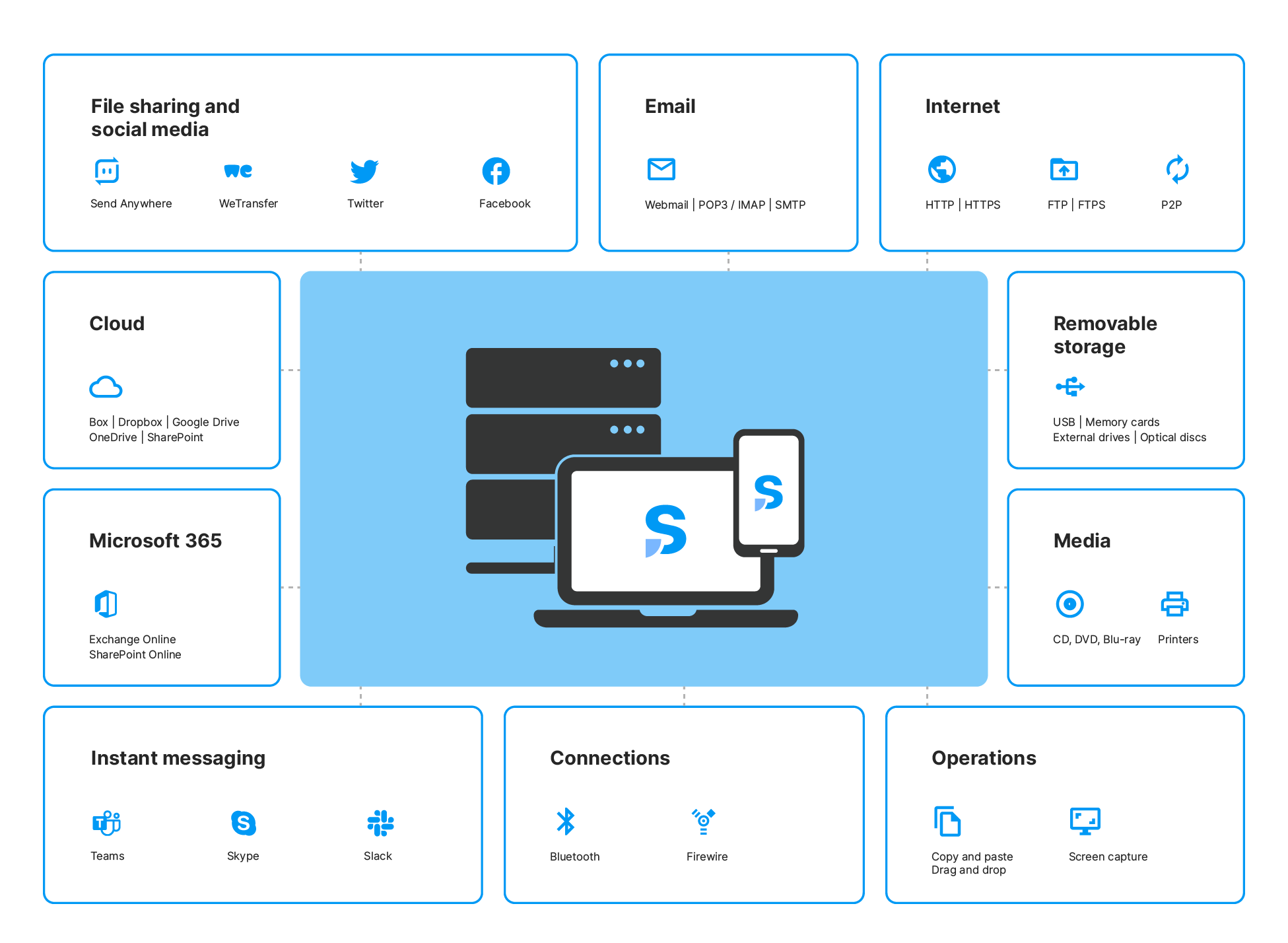
In the past, company data was stored on paper – in files and folders in offices and archives. During the process of digitization, all data was moved to digital formats. Data can be found and moved via the following channels (both official and unofficial):
- File sharing websites and social media (WeTransfer, Twitter, Facebook, Send Anywhere)
- Email (Webmail, POP3 / IMAP, SMTP)
- Internet (HTTP, HTTPS, FTP, FTPS, P2P)
- Cloud (OneDrive, Dropbox, Google Drive, Box, SharePoint)
- Microsoft 365 (Exchange Online, SharePoint Online)
- Instant messaging (Teams, Skype, Slack)
- Removable storage (USB, Memory cards, External drives, Optical discs)
- Media (CD, DVD, Blu-ray, Printers)
- Connections (Bluetooth, FireWire)
- Operations (Copy and Paste, Drag and Drop, Screen capture)
Why you should protect data
Insiders don’t treat data with care
Insider threats are on the rise due to trends in digital workspaces, flexible and remote work, and agile and BYOD approaches. The overall number of incidents has increased by 44 percent in the last two years. Most of these threats are unintentional – 56% were caused by negligent insiders, whereas 26% were malicious.
Read more about insider threats here.
Data ends up in a competitor's hands
Data has great value for companies and can easily generate another revenue stream. There are even companies whose business is based on data generation. So, employees might be motivated to steal a company’s data and sell it to competitors or other companies.
Reputation risks for a company
When a data breach occurs, a company’s reputation is at risk. Negative media coverage can lower the number of customers, and hence lower profit.
According to the US National Cyber Security Alliance, about 60 percent of small businesses close within six months of a major data leak and 85% of companies experience a data breach.
Data breaches caused by insiders are very costly
The costs of breaches can be enormous. The overall costs of an insider threat incident have increased from $11.45 million in 2020 to $15.4 million in 2021. The longer it takes to detect an internal threat, the higher the costs. On average, it takes nearly three months (85 days) to contain an insider threat incident. Incidents that took more than 90 days to discover cost companies $17.19 million, the average cost of incidents that were discovered in less than 30 days was $11.23 million.
Regulatory compliance and GDPR
In the event of a data breach legal authorities may impose fines. The strictest regulation is GDPR. Companies that violate GDPR can expect the following fines:
- The lower level is up to 10 million euros, or 2% of the worldwide annual revenue from the previous year, depending on which is higher.
- The upper level is up to 20 million euros, or 4% of the worldwide total revenue from the previous fiscal year, depending on which is higher.
Read more about GDPR in this article.






How companies lose their data
As stated above, the majority of insider threats are unintentional and occur for various reasons, such as hybrid modes of working, or BYOD approaches. Insider threats can also happen because employees are tired, work under stress, or are not aware of the security processes and importance of data security.
Let’s have a look at a few real-life situations that will show you how insider threats are a part of daily business operations.
James is rushing to kindergarten
James needs to pick up his child and doesn’t have enough time to update the customer database for the next day’s emailing. He might be able to do it from home, but according to the company’s policies, it is not possible to log in without a VPN. And he has just bought a new laptop but hasn’t set up the VPN yet.
Meanwhile his child is crying, and the teacher is calling James to see if he’s on his way. He is in a rush, so he copies the Excel sheet and uploads it to his personal Google Drive and decides to do his work at home in the evening. But his Google Drive is full of photos from his vacation and there’s not enough free space to upload the Excel sheet. So James uploads it to WeTransfer. With no encryption and no password.

Laura was interrupted by a colleague while sending out an email
Laura is working on an important email with financial documents for her company’s CFO, when suddenly her phone rings. It’s her colleague with an important issue that needs to be resolved right away. Laura is on the phone with her colleague when selecting a recipient’s email address. She is under pressure and therefore instead of the CFO’s name, she chooses the client’s email address from the suggestion.

Charlie doesn't enjoy his job anymore
Charlie has issues with his manager and decides to find a new job. He is talented and has already received an offer from a competitor. Charlie knows that his company’s client database will be helpful in his new job and decides to take it with him. He thinks it’s risky to send it via email, so he uploads a few screenshots and database exports to his USB drive.

As you can see from the examples, insider threats mostly don’t have malicious intentions, however, the consequences might be as harmful to a company as a malicious act would be.
Whose hands your data might end up in
- Hackers/ransomware groups might blackmail you, threatening the data will be published unless you pay some money to them.
- Competition would be one step ahead of you in case they get access to your customers’ data, business plans, or know-how.
- Contractors would be negotiating lower prices because they would be aware of your conditions, calculations, and margin.
How to protect your company's data
No matter how many channels your company uses, there are a few universal ways of protecting your data.
- Perform a data audit and find all your sensitive data. It is good to know what type of data your company operates with, where the data is stored and who has access to work with it or can change it.
- Implement policies that specify how sensitive data can be handled and who can access it and for which purposes. Make sure your policies are easy to understand.
- Educate your employees and explain to them the importance of data security. They should be aware of what type of data your company operates with and what are the consequences of misusing it.
- Encrypt your data and make sure that even if you lose your flash drive or phone your data will remain safe.
A few more data security tips:
- File sharing websites, social media and instant messaging – Block upload of the data, or notify employees about risky operation
- Email – Restrict sending data to unknown external email addresses, notify employees about potential breach
- Internet, cloud, O365 – Restrict uploading data to unofficial channels outside the company or notify employees
- Printers – Check what type of documents your employees print based on contextual information and discover potential data breaches; restrict printing specific sensitive documents
How Safetica protects your data
Monitors your data flow
Safetica offers features to track and protect various data flow channels your company uses. Safetica checks your company’s outgoing communication channels and gives you an overview of how data travels in your company. Once you know your data flows you can set security measures. Notify your users about risky behavior or block dangerous file sharing actions.
Helps you to be compliant with regulations
Safetica helps you to monitor the data flow within your IT environment as well as when it leaves the perimeter of your company. You can set specific rules that help you to comply with GDPR or other data protection regulation. You will be able to see how employees work with personal and other sensitive data, and it allows you to eliminate the risk of misuse or accidental policy violation. The system notifies you in real-time in the event of a security threat.
Encrypts your data
Safetica gives you the option to manage encryption of USB devices and disks using BitLocker. The solution takes care of security key management and recovery.
Protect your data against insider threats
Safetica checks the users’ behavior and notifies you when finds anomalies. In case a user starts to send bigger amounts of data at night or works with different types of data out of a sudden, there is a potential incident, and the system notifies you, and you can take appropriate action.
Safetica notifies employees about risky operations, hence educating them about data security. It is important to trust your employees, however, let’s not forget we are all people, and people make mistakes. Safetica mitigates these risks, and you can go to sleep in peace knowing that data, people, and your company are protected.

Next articles

Hidden Data Everywhere: Why It’s Important to Have Complete Visibility for Data Security
Modern work creates blind spots across shadow IT, AI tools, personal devices, and third-party services. This article explains why visibility is essential for effective data discovery and stronger data protection.

